Layered security
Layered security, also known as layered defense, describes the practice of combining multiple mitigating security controls to protect resources and data.
Like all other security methods, layered security is designed to protect assets (an asset is anything you want to protect and can include people, property, data, etc).
Layered security can be used in any environment, from military operations, to individuals, and community residents (homeowners, neighborhood watch groups, etc).
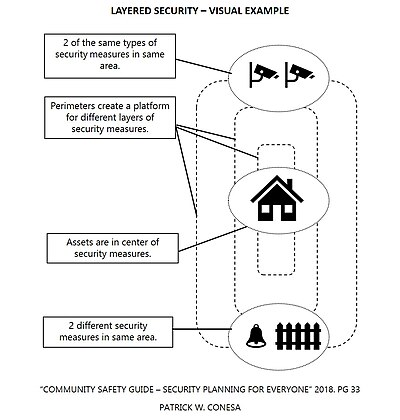
In other words, "layered security is the practice of using many different security controls at different levels to protect assets. This provides strength and depth to reduce the effects of a threat. Your goal is to create redundancies (backups) in case security measures fail, are bypassed, or defeated. Placing assets in the innermost perimeter will provide layers of security measures at increasing distances from the protected asset. The number of layers and the security measures you use, will depend on the threat and importance of the asset".[1]
The term bears some similarity to defense in depth, a term adopted from a military strategy that involves multiple layers of defense that resist rapid penetration by an attacker but yield rather than exhaust themselves by too-rigid tactics. As the incursion progresses, resources are consumed and progress is slowed until it is halted and turned back. The information assurance use of the term "defense in depth" assumes more than merely technical security tools deployment; it also implies policy and operations planning, user training, physical access security measures, and direct information assurance personnel involvement in dealing with attempts to gain unauthorized access to information resources. Within a defense in depth security strategy, layered security is regarded by some[who?] as merely a delaying tactic used to buy time to bring security resources to bear to deal with a malicious security cracker's activities.
Philosophy[edit]
Layered security is an example of the Swiss Cheese model (or "cumulative act effect"), used in risk analysis and risk management. In this model, security systems are likened to multiple slices of swiss cheese, stacked side by side, in which the risk of a threat becoming a reality is mitigated by the fact that it must pass through "holes" in the defenses (i.e. not be trapped and detected by each different defense), and these defenses are of different kinds, and locations that are "layered" behind each other. Therefore, in theory, lapses and weaknesses in one defense do not easily allow a risk to materialize, since other defenses also exist, to prevent a single point of weakness.
Commercial[edit]
For every category of threat, there should be an effective control deployed to mitigate the threat. Security vendors will sometimes cite differing solutions, but most can be grouped under consumer or enterprise categories:
Consumer Layered Security Strategy[edit]
- Extended validation (EV) SSL certificates
- Multifactor authentication (also sometimes known as versatile or two-factor authentication)
- Single sign-on (SSO)
- Fraud detection and risk-based authentication
- Transaction signing and encryption
- Secure Web and e-mail
- Open fraud intelligence network
Enterprise Layered Security Strategy[edit]
- Workstation application whitelisting
- Workstation system restore solution
- Workstation and network authentication
- File, disk and removable media encryption
- Remote access authentication
- Network folder encryption
- Secure boundary and end-to-end messaging
- Content control and policy-based encryption
Integrated Solutions[edit]
An "ad hoc" security strategy, with numerous vendors and an abundance of different, sometimes incompatible security solutions and products can leave gaps in protection, whereas a vertically integrated vendor stack could provide more comprehensive defense. Single-vendor solutions improve interoperability between components of a complete security strategy, and may offer performance and price benefits over a multi-vendor approach.[citation needed]
Best Of Breed Solutions[edit]
The contrasting commercial security product argument is that a "best of breed" approach provides more effective protection. While a single vendor's vertically integrated product stack may be the offering of choice for vendors who want to monopolize a client's or customer's business, it could also be argued that each component of a comprehensive security strategy should be evaluated both for its performance within its niche and its open compatibility with other, non-integrated components of the whole.[citation needed]
References[edit]
- ↑ Conesa, Patrick (2018). Community Safety Guide: Security Planning for Everyone. amazon.com. p. 33. ISBN 978-1719441582. Search this book on

This article "Layered security" is from Wikipedia. The list of its authors can be seen in its historical and/or the page Edithistory:Layered security. Articles copied from Draft Namespace on Wikipedia could be seen on the Draft Namespace of Wikipedia and not main one.
